GET STARTED TODAY
IT Security & Cyber Security Awareness Training
Why Cyber Security Training Is Important
No matter how much you spend, no matter how complex the technology, no matter how rigorous or punitive the compliance requirements are, investments in technical cybersecurity mitigation measures by themselves will never be enough.
Even if your cyber security defenses in place stop 99.9% of all attempted data breaches, it can take just a single click on a malicious link by a distracted employee, such as through phishing emails, to lock up your entire system or to introduce damaging viruses.
As much faith as we have in our employees to be vigilant against cyber threats, responsible companies must nevertheless plan for lapses and put in place rigorous and ongoing training and awareness programs.

What Is Cyber Security Awareness Training?
Systems and data are not always targeted directly during a cyberattack. Oftentimes, people are targeted first and used to gain unauthorized access to systems and data.
Cyber security awareness training educates the people within an organization on common cyber security threats and how to avoid them. An effective cyber security awareness program will provide ongoing training to ensure personnel know and follow security policies, procedures, and best practices.
What Are the Benefits of Training in Cyber Security?
Providing cyber security training is an essential part of any security program. And there are many benefits to a workforce that is well-prepared to face digital security threats, including:
- Better compliance – Employees who are kept up to date on evolving security policies, procedures, and regulations are more likely to comply with those requirements.
- Fewer incidents – When employees know what to look out for, they're less likely to fall victim to social engineering attacks. And when everyone knows and follows best practices, security across the entire organization will become more robust.
- Increased productivity – When everyone is on the same page regarding security procedures, there is more synergy among teams and between departments, keeping operations running smoothly.
- Rapid response and recovery – When a cybersecurity event does occur, heightened awareness empowers everyone to respond promptly and appropriately, mitigating damage, loss, and other undesired effects.
Our Cyber Security Training Program includes the following services
Unlimited Phishing Security Tests
Automated Security Awareness Program
Security ‘Hints & Tips’
Training Access Level I
Automated Training Campaigns
Crypto-Ransom Guarantee
Phish Alert Button
Phishing Reply Tracking
Active Directory Integration
Training Access Level II
Monthly Email Exposure Check
Vishing Security Test
Smart Groups
Social Engineering Indicators
EZXploit™ - “Automated Human Pentesting”
USB Drive Test
Vulnerable Browser Plugin Detection
Priority Level Support
Training Access Level III
AIDA™ Artificial Intelligence-driven Agent BETA
One Time Training Isn't Enough for Cyber Security
It’s not enough to put new and existing employees through a 1 hr security training session (perhaps mingled with company history videos, performance expectations, harassment training, etc) and expect perfect execution to counter potential hacks or damaging security incidents.
In the course of a busy work day, a very official looking email could come in from a spoofed executive account, “authorizing” the release of funds, or requesting a password or special phrase.

To Learn More About Our IT Security & Cyber security Awareness Training, Request A Consultation.
Continuous Cyber Security Awareness Training
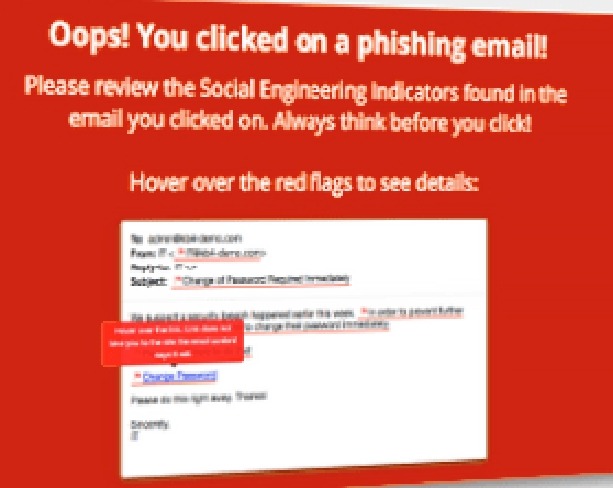
These data breach tactics evolve in sophistication every day, and so we all need to be kept aware of threats in general as well as how it might now present itself. To help keep our clients informed of the threats of today (and tomorrow) RSI offers comprehensive web-based security awareness training that integrates formal training programs with mock phishing attacks that simulate the look and feel of a real social engineered attack.
Given the potential damage of a breach, security concerns need to stay top of mind for everyone in your organization, for such our mock attacks are deployed at random, in various forms. If the employee falls for one of these simulated attacks, an administrator is informed, setting up an opportunity for further training and to understand broader context of why the breach was made possible.
Was the employee simply distracted? Was the attack messaging type new and unique? Was it guised in official looking documents such as a Microsoft Word file? Was it a link hidden in a FedEx tracking email? Whether pass or fail, our training programs provide valuable metrics to company administrators to understand their specific threat attack surface, and can provide insights on how to proactively counter future breach attempts and keep sensitive data away from those with unauthorized access.
RSI Security Can Help
These data breach tactics evolve in sophistication every day, and so we all need to be kept aware of threats in general as well as how it might now present itself. To help keep our clients informed of the threats of today (and tomorrow) RSI offers comprehensive web-based security awareness training that integrates formal training programs with mock phishing attacks that simulate the look and feel of a real social engineered attack.
Given the potential damage of a breach, security concerns need to stay top of mind for everyone in your organization, for such our mock attacks are deployed at random, in various forms. If the employee falls for one of these simulated attacks, an administrator is informed, setting up an opportunity for further training and to understand broader context of why the breach was made possible.
Was the employee simply distracted? Was the attack messaging type new and unique? Was it guised in official looking documents such as a Microsoft Word file? Was it a link hidden in a FedEx tracking email? Whether pass or fail, our training programs provide valuable metrics to company administrators to understand their specific threat attack surface, and can provide insights on how to proactively counter future breach attempts and keep sensitive data away from those with unauthorized access.
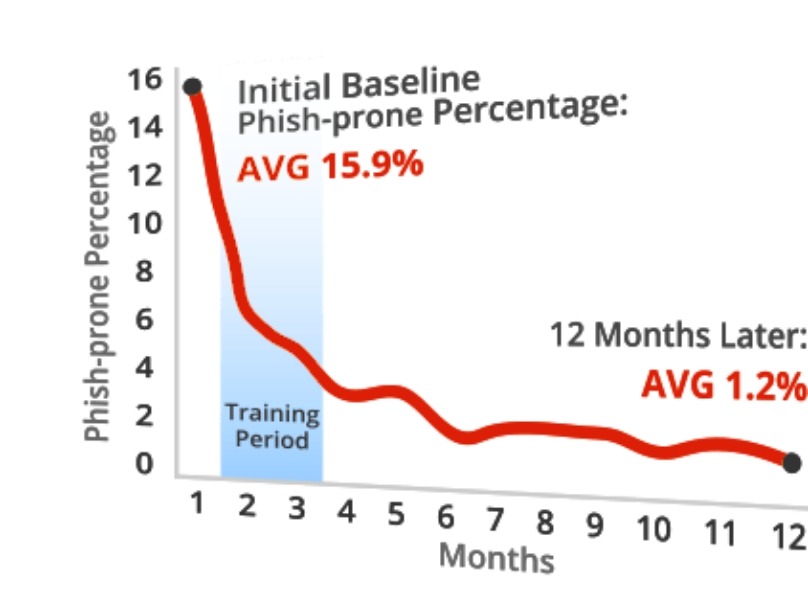
Cyber Security Awareness FAQs
The necessary details of a cyber security training program will vary depending on the needs of an organization. However, any comprehensive training should include education on:
- Basic IT concepts
- Common cyber security threats
- Incident prevention and mitigation techniques
- On-site and remote security best practices
- Security policies and procedures
The costs of a cyber awareness training program will vary depending on the contents of the program, the size of the organization, and other factors. Maintaining ongoing cyber security training for employees may seem like a hefty investment, but the recovery and legal costs of an incident would be much more significant. Ongoing training is critical and RSI Security will help you form a program that fits your organization's needs and operational budget.
Frame cyber security best practices as a collaborative effort. Learning how to safeguard systems and data is something everyone can do to help the organization and those you serve.
Besides highlighting how it adds value, promote the fact that knowing and following cyber security best practices will be beneficial in employees' personal lives.
The first step is assessing what needs to be included in an initial cyber security awareness program. Implement it with the following points in mind:
- Clarify policies and procedures – Ensure employees know what security procedures they are expected to follow.
- Explain why it matters – Let employees know why the organization may be targeted, the impact it could have, and the responsibility to prevent incidents.
- Focus on actionable steps – Teach employees how to recognize suspicious activities, how to secure their activities, and what to do when something goes wrong.
- Introduce primary security personnel – Ensure all personnel know who to reach out to if they have concerns or if an incident takes place.
- Keep training accessible – Don't overload trainees with too much at once. Present information in a way that's easy to understand and provide it in multiple formats so that nobody is excluded from accessing it.
- Assess and make adjustments – Use monitoring, penetration tests, and other assessments to evaluate the efficacy of the training program and improve it as needed.
RSI Security's cyber security training services are tailored to your organization's IT infrastructure and security needs. Alongside an ongoing training program, we provide tools for testing, monitoring, and updating training for robust, future-ready security.
Everyone has a part in upholding an organization's digital security, so training should be required for all employees. If there are contractors, partners, or other parties with access to systems and data, they should also receive training to ensure awareness and compliance with your organization's cyber security program.
There's no prerequisite for cyber security training. Every employee within an organization can benefit from and should participate in IT security awareness training.
CUSTOMERS
Organizations that trust RSI Security










Request A
Consultation for Cyber Security Awareness Training